Last updated on 23 June 2021
This will be my two cents on helping people obtain a foothold in the infosec industry. This post might get pretty lengthy, so grab a beverage, relax and enjoy my two cents on the matter.
DISCLAIMER: It should also be mentioned that NONE of the resources mentioned in this post sponsor or endorse me in any way. So you can rest assured that my opinions, are my real opinions.
DISCLAIMER2: Everything written here is based on my own experiences, so yes, there will be bias, however I tried to remain relatively objective.
The driving factor

The first thing I’d like to address is a very personal question, which I urge you to ask yourself.
“Why are you doing this?”
If the answer to that question is in the line of "Because I want to hack my ex's social media" or "Because it looks cool" or "Because I watched mr. Robot and/or played Watchdogs"
Let me stop you right there.
Pentesting, and especially red team operations, is a field which will require constant studying. You will face a lot of different challenges, and if your mindset isn’t right, you will not survive long in this industry.
The reality of infosec is nowhere near the image it has gotten from video games and/or Hollywood productions. The term cyber warfare comes to mind, just like in the army, this profession will ask a lot of you both physically (due to time you’ll need to allocate to advance in your tradecraft) and mentally.
Enough with my rambling, moving on..
A hackers’ skillset.

Just as in life, the cards are not equally balanced. Some people will grasp deeply technical concepts quicker than others, and your background plays a part on how much time it will take to get in, and advance in the industry.
However, I believe that, with the right state of mind, you can achieve anything. Even entering this field without any prior knowledge.
A non exhaustive list of skills that will help you in this industry (in no particular order) are the following:
- Programming experience : doesn’t really matter which language, as long as you grab the concepts of both script style programming as object oriented programming.
- People skills : not only will this help you build a network of like minded people, it will also help you in social engineering attacks.
- Dedication: this one speaks for yourself.
- Logical and creative thinking: you will need both parts of your brain to exploit the world. Not all exploitation paths are straightforward. You’ll often find yourself thinking out of the box.
- A desire to understand how things work, on a very deep level: Luckily for us, the infosec field has a ton of good researchers, publishing their work for free. However, if you ever want to write your own exploitation tools/chains, you will often need to do heavy lifting, reading technical documentation such as API documentation and RFP’s
As you can see from this brief list I made, some of these things are not really “learnt”, they just have to be part of who you are as a person.
Honing your skills – Preface.
I think this is pretty much the core of this blogpost, and probably the reason why you are reading this post. What resources are there and what do I recommend.
I wouldn’t be a good consultant if I didn’t answer that question with an IT classic: “it depends”. Infosec is huge, you have blue and red teams, purple teams and a whole bunch of penetration testers in between. You have mobile assessments, web assessments, fat client assessments, code reviews,… the list goes on and on…
However, dispair not. I will share what I think are solid resources to build foundations (that will apply to any of the sub branches of infosec you want to take) and, finally, I will expand upon red teaming operations, as this blog is supposed to be about red teaming.
Honing your skills – a good house needs solid foundations.
In this section of the blogpost, I will go over my own biased view of some of the absolute must haves if you wish to start (or advance) in your infosec carreer.
Coding experience
There are a ton of good resources online to start learning how to code. Some examples of these are (and I’ve personally used these in the past) code academy and edx. Some udemy courses are also quite nice, but a lot of udemy courses are pretty subpar, so be careful with those. If you have some extra cash, I can also recommend pluralsight, but as far as I know they don’t really have free content.
Hacking experience
The most important aspect of learning is not only reading about it on a high level, but getting your hands dirty! Luckily there are some cool platforms to help you out. I’m a big fan of Hack the Box and VulnHub, I also know about tryhackme but I’m sure I’m leaving out other great resources.
Learn from the best and brightest.
When I started in infosec, there was one consistent persona that I learned a ton from, and he might ring a bell to many of you: ippsec he mainly covers hack the box videos, but does so in a way that is relatively easy to follow, even for beginners in the field. I can promise you, just watching this guy and really paying attention, will certainly be worth your time investment.
Later on, another personality came to my attention: The Cyber Mentor he covers a ton of different content and because of this, I’m quite confident that you’ll find something interesting in his videos, no matter what sub branch of infosec you have interests in. I should also mention that he has excellent beginner friendly udemy courses, and also some interesting stack based buffer overflow youtube videos, which will prove to be very useful should you decide to tackle the OSCP.
Other resources, I can recommend, albeit their content is somewhat more advanced:
The Wover
RastaMouse
XPN
Vincent Yiu
Spotless(ired.team)
CPL3H(ijustwannared.team)
Batsec
And I’m probably forgetting a billion others. Sorry folks, can’t list all of ya. Know that I respect and love you all none the less!
To end this, I’d like to also mention that attending conferences or following them over live stream is a great way to learn state of the art techniques. Definitely keep an eye out for Defcon (and others)!
Trainings
There are a ton of great trainings online, but most of these are dedicated to specific sub branches of infosec (web exploitation,windows exploitation malware development,…)
However, two (three if you include SANS) platforms stand out that cater to all branches of infosec, in varying difficulty:
ElearnSecurity

I’m going to be fully honest, at first I didn’t expect much of eLearnSecurity. I thought there courses were very lightweight technically and that there certifications they offer are useless due to their relatively low price point, compared to their competitors.
However, they are continually updating their courses and I must say I’m pleasantly surprised by their new and improved Penetration Testing Extreme course.
They are definitely worth an honorable mention now, as they cater to both defensive as offensive sides and their pricing is relatively democratic compared to SANS for example.
Pentester Academy (formerly known as SecurityTube)

Again, full disclosure. I’m a huge fan of pentester academy. Sorry 🙂
You will not hear a single bad word (okay, maybe a little one in the end) from me about them, at a price point of 39$/month or 249$/year they offer top notch content and the instructors they managed to get to lead the classes are world class (Nikhil and Vivek, to name two).
They have about 40 different courses, from beginner level to advanced, and they also have an online lab with a seemingly endless (1700+, according to the site) exercises.
They also offer red team certifications (sold separately, more about that later in this post.)
The only downside to them is the marketing, they seem to have a “sale” going on forever… which is in my opinion a pretty cheap marketing trick to convince people to buy a subscription…
I don’t really see why, as their courses speak for themselves: top notch content, for pretty low prices.

SANS, and why it gets its own subsection!

I wanted to give SANS it’s own subsection in this post for two reasons:
- Nothing compares to the quality of SANS courses, literally NOTHING
- Literally nothing compares to the cost a SANS course has, literally NOTHING
SANS is freaking awesome, and if you have the chance to ever follow one of their training, take it, and never let go! They have over 65 trainings ranging from management trainings to blue team training to red team training to everything in between, you name it, they have it.
The problem is, as an entry level, unless you land a job at a big firm, you’ll probably not going to get the cash together to follow a training. SANS trainings typically costs over 5k USD and that is without travel + accommodations.
If you manage to arrange a work/study contract with them though, SANS could be very beneficial. That contract means you would be a facilitator (an instructors assistant, during the entire course week). As a reward for your “hard” work, you get a massive discount on your course (bringing the cost to about 2.5K USD) and you’ll get a free certification attempt (if your course has a certificate option).
On top of the training, SANS also hosts “NetWars”, which is a brutal CTF where you compete against your fellow hackers, and you can be rest assured that the people participating have mad skills, as people that do SANS courses are usually battle hardened veterans.
Finally, to top it all off, SANS does have a lot of free resources available, and regularly host free webcasts as well, usually the topics are very interesting, and I would highly advise all of you to keep an eye on their website.
For red teaming operations, I would advise the following SANS courses (in no particular order):
SEC560, SEC564, SEC599, SEC699, SEC617,SEC660 and last but not least, SEC760
That being said… It’s time to….
Put your money where your mouth is, time to certify!
The gatekeeper certification – OSCP
Ah.. the OSCP. Feared by many, but in my opinion misplaced. I call OSCP the gatekeeper of infosec. The reason being that OSCP is an exam that teaches you how to use Kali and forces you to start implementing some sort of methodology.
As an added bonus, OSCP is a proctorred exam with a solid team actively permabanning people that leak exam answers. Making this exam essentially cheat proof.
Although OSCP is primarily focused on infrastructure (owning kali and windows machines) it touches base with web application and exploit development (stack based buffer overflow).
If you have good foundations, as outlined previously in this blogpost,OSCP will be relatively easy to obtain, which opens a lot of (HR) doors to land your first infosec gig.
My personal advise: if you really want to do a certification, and can only do 1, do this one.

I passed OSCP!! What do I do now?
Well, that is honestly completely up to you. As I already mentioned, SANS has a ton of training and certifications. Offensive Security has some other certs you can persue, it all comes down on what path you want to take and what interests you the most. As this is a red teaming blog, I’m going to be discussing red team oriented certifications from this point on.
So if this is where I’m losing your interest, thanks for reading! if not, let’s move on!
Certified Red Team Professional – The gatekeeper for infrastructure pentests
Even though the title says “Red Team” professional, I actually kind of think of this certification and training as more of an internal infrastructure pentest scenario. There is a ton of overlap between this certification and RastaMouse’s “Certified Red Team Operator” certification.
However, I like them both and see them as complementing each other instead of competing with each other. In this course you’ll get access to a lot of video material authored by Nikhil. He explains core concepts in such a way that they become relatively easy to understand, and he even guides you along the lab over video, which I thought was pretty unique and pretty cool.
The main reason why I’m putting this certificate as a internal infra test over a red team cert, is because in this course, you will not learn to use a command and control server.
You’ll work with reverse shells, webshells and port proxies, learn about constrained language mode and applocker, and a ton more… which is all pretty cool, as these foundations will help a lot to when you make the transition towards a more red team oriented approach, as command and control servers use these tactics “under the hood”.
Certified Red Team Operator – The gatekeeper for red team operations
In my opinion, this cert is to Red Teaming what OSCP is to Pentesting. This course is written and actively maintained by RastaMouse himself. It cover a wide array of core principals that a red team operator should have and is strongly focused on compromising a network from an external point of view, using C2’s (currently the course has in depth instructions for Covenant and Cobalt-Strike).
In this course you’ll touch the following topics:
- Introduction to red teaming
- External Reconnaissance
- Initial Compromise
- Host Reconnaissance
- Persistence
- Local Privilege Escalation
- Domain Reconnaissance
- Credentials & User Impersonation
- Lateral Movement
- Session Passing
- SOCKS Proxies
- Reverse Port Forwards
- DPAPI
- Kerberos Abuse
- Group Policy Abuse
- MS SQL Server Abuse
- Domain Dominance
- Domain & Forest Trusts
- Bypassing Defences
- Complete Mission
- Wrap Up & Post-Engagement
The best thing is: If you have OSCP, You can skip the entire lab and instantly go for the exam instead. I however, do NOT recommend this approach as you’ll be missing out on the course material which will get updated for free on a pretty regular basis for anyone that has ever bought the course. Pricing is pretty cheap too, the OSCP approach (no courseware) costs 149 GBP, the courseware approach costs 399.00 GBP. In addition to getting access to the courseware you’ll also get an invite to a slack channel where you can discuss with your fellow peers and even with the big Mouse himself, if you’re lucky enough to be deemed worthy of his time (the man is very busy, but very friendly!).
A quick note, if you do decide to go for the courseware approach, you are REQUIRED to complete the entire lab IN ADDITION TO passing the exam. Passing the exam alone is NOT enough to get this certification!
I really enjoyed this certification, and I’m not lying if I could see this one becoming the new standard for red team vacancies.
Certified Red Team Expert – The professionals cooler brother.

If you have the foundations down and want to progress further into honing your skills, I can recommend this certificate. This certificate is catered to people that have already experienced a few infrastructure engagements, and as a result, will not have much new course content in comparison to what you’ve received in the professional certification course.
However, what this certificate loses in course ware, it makes up in hands on experience ! Students get the opportunity (but are not forced) to do a CTF like lab to practice their skills, and for that reason alone, I think it’s worth the cost.
There are about 60 flags to collect, and some of them are pretty damn challenging to extract, even for a battle hardened red team operator. This has nothing to do with the technical difficulty, but because it behaves more as a CTF so it requires some digging around.
However, because of this, it forces you to think more outside the box.
I’d like to advise you, if you are going to take this exam and course, to also take a look into the pentester academy subscription, as the SQL server abuse course will come in very handy in both the CTF lab as in the exam.
I think this cert is nice to chase, if you want to dive deeper in how all your tradecraft tools work under the hood and just to obtain some experience, as this lab will keep you going for days!
The Exam itself is relatively smooth sailing, but has some “nasty” surprises along the way 😉
OSCE – The sensei of the certificates.

OSCE… boy oh boy…
The course is ANCIENT. I’m not going to lie about that, but almost everything you learn in this course is applicable to today. A stack remains a stack, registers remain registers, and assembly hasn’t really changed a lot over the years. I’m still in the process of finishing this certification, so I can’t really divulge much more into it’s contents. All I can say is, I’ve heard that the course will get updated sooner than later, and the content and cert is great if you ever want to write your own exploits.
If you decide to persue this certification, I highly recommend taking the Linux Shellcoding X86 course on Pentest Academy (previously called SLAE) as Vivek teaches you core concepts useful to advance in the course faster.
Another useful resource that will guide you through OSCE is this one:
https://tulpa-security.com/2017/07/18/288/
Certificate Wise, that’s it. I don’t have any other certificates to talk about as I simply don’t have any others. And I don’t believe into giving advise without having the millage to back up my claims. As a result, I cannot give any other advise certificate wise.
My own wishlist
Here are some certs and trainings that I want to follow, but have not had the opportunity to do so yet. The reason I’m including these is because they might be interesting for like minded people that already have a firm grasp on red teaming.
PACES – The final Pentester Academy Red Team certificate:
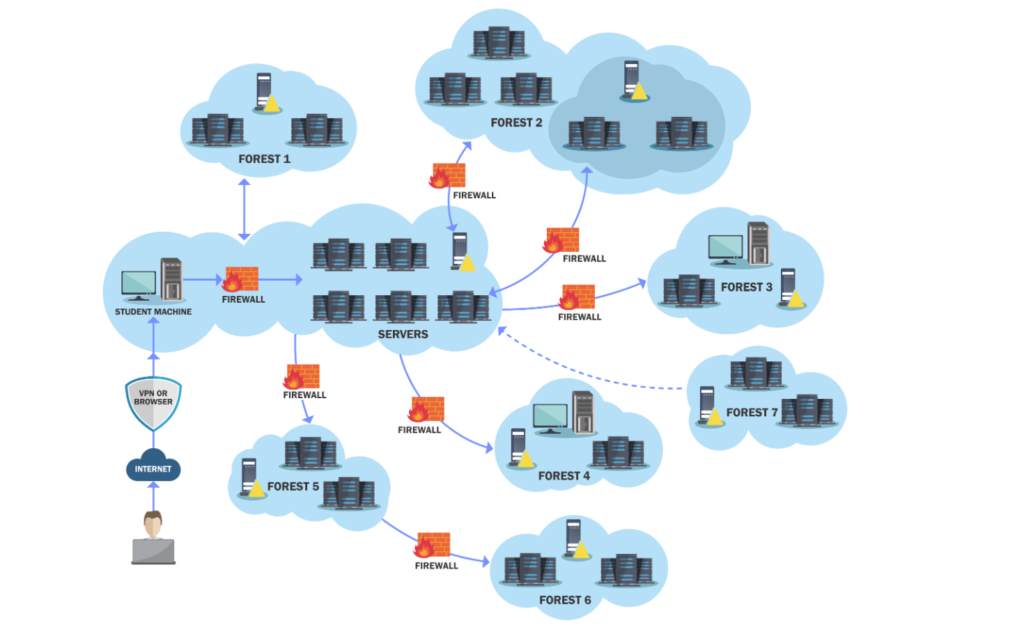
Look at how majestic their lab is. I want to pwn it, desperately. From what I’ve heard, this lab is an excellent playground to test out new stuff as it has a detection stack. It also touches base to the blue aspect, as you will have to attack and defend in the final exam. I think it’s pretty damn cool. This is a quote directly from the website
GCB enables enterprises to simulate actual adversaries by focusing on goals rather than just getting privileged access to machines. For effective adversary simulation and exciting gamification, the end goal of GCB is to initiate a fake transfer of funds from the target bank.
INITIATE BANK TRANSFERS? COUNT ME IN!
MDSEC – Advesary Simulation and Red Team tactics
This is a three day course thought by the legendary duo Dominic Chell and Adam Chester (XPN). These guys know what’s up. I’m a big fan of them both and they got me hooked with the following quote:
You will learn how to write your own advanced initial access payloads, equipped with strategies to bypass modern EDP/EDR solutions including PPID spoofing, argument confusion, blocking of third-party DLLs, AMSI bypasses and how to remove userland hooks.
Bypassing modern EDR? It can never hurt!
Corelan – exploit writing
If you never heard about Corelan, you must have been living under a rock. Seriously, they are Belgian based, (so am I), and they created mona, which helps TREMENDOUSLY to write your own exploitation chains. Yup, They don’t need to pitch me anything, I’m already hooked and I have never even talked to any of these legends yet.
Interesting, many people want to Red Team but will be so disappointed when they find them selves trying to find a 100 % Red Team. Most will be at best Purple Teams.
Too many will be glorified Auditors.
On paths there are a few into Security:
• Technical (Red Team)
• Audit (verify)
• Managerial (Blue Team)
This said we all need to respect those who have gone before us as well as those who follow.
Agree it is a moving target and SANS is good training, especially if local. On costs in the article they need a bit of an update. In the long run will soon become out of reach for a candidate screening method.
Iain
Awesome Post very helpful and great to follow for starting in Red Team. Thanks!
[…] submitted by /u/jeanc0re [link] [comments]Post […]
Thank you for this article. It was useful and informative.
I want to become a whitehate hackery
Amazing article/blog! Thank you so much for writing this! I’ve always wanted to have a real security job but I always end up going to infra jobs like devops. I like it though but I wish I had more knowledge in security. I really want to pursue to become really good in security but I am not sure where I should focus.
[…] articles I found to be interesting and fairly succinct in their presentation. Specifically this one from Jean-François Maes and this one by John […]
What a top quality info , literally masterpiece
Thank you very much for the knowledge sharing and your pov about that magnificent pentest world. I want to prepare myself to oscp asap and achive that dream
Wish you the best my friend
Jhonny