A few weeks ago, I noticed a cool post:
https://ired.team/offensive-security/credential-access-and-credential-dumping/credentials-collection-via-creduipromptforcredentials
This seemed like an interesting approach to potentially provide a “final shot” when you are getting very desperate during an engagement. The problem was, the PoC on the website was not compatible with post exploitation C2 operations in memory. So I decided to give it my own swing and code it in C#
The Tool can be found here:
https://github.com/WingsOfDoom/ICU
The Tool will pop up a Windows UI style credential box, default I added Outlook text, but this is arbitrary and can easily be swapped to something else. It looks like this: (Of course this is now being locally ran, but in reality this would be injected).
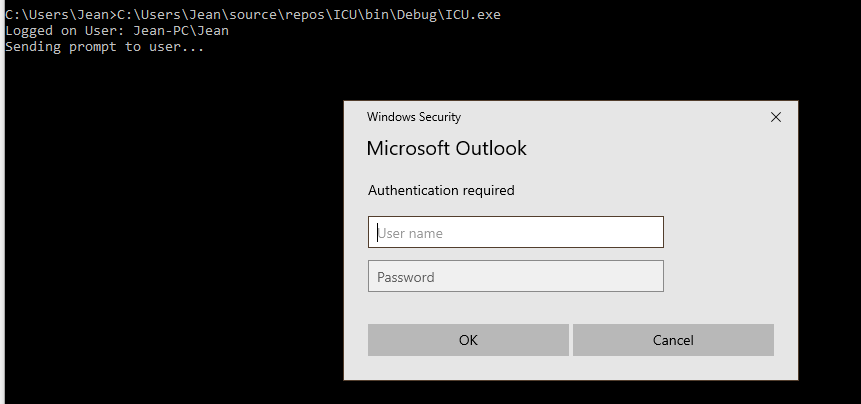
It essentially uses LogonUser to validate the credentials, if the logon fails, the prompt will keep popping up until the right credentials are provided or the user cancels the prompt themselves. All logons are being returned even the failed ones, as sometimes users can mix up their passwords and actually provide a password intended for another application.
The code is open source, so feel free to fork and adapt to suit your own needs.
As already mentioned, this is a Hail Mary, and should only be used when you are deadstuck and are about to give up your efforts, as your chances of detection will increase drastically. This could however potentially be used in an elaborate social engineering scheme where you can convince a user that an administrative user credentials are needed. Potentially compromising a high privileged account, think helpdesk scenarios in big firms.
Be First to Comment