In the light of the fairly recent NOBELIUM ransomware and through some red team experience of my own, I figured it was time to release a tool called Lnkgen available on GitHub: https://github.com/jfmaes/SharpLNKGen-UI
Preamble (skip if you are not fan of stories/jokes)
The art of hiding payloads in lnk files is ancient. However, as we have seen recently the awareness around lnk’s is also “ancient” as in people don’t know about the threat or they simply forgot (or don’t care).
LNK generators have been around for a while as well on underground forums and from malware-as-a-service (MAAS) providers.
I had written a LNKGenerator in the past as a CLI tool, and decided it would be a fun little challenge to port it over to a (somewhat) user friendly GUI.
My first thought was to port it over to dotnetcore and use Avalonia UI to make it cross platform. I quickly backed off from that one though as Avalonia although quite cool, is fairly complex for the uninitiated and I could not find a decent file browser dialogue binding (Okay, I was just lazy).
So I went to another ancient technology instead, WINDOWS FORMS. Yes, you read that right, Windows Forms. Why you ask? Well it has drag and drop building blocks, and again, I AM LAZY OKAY, It’s super hot where I live and my airco has not arrived yet 🙁
Introducing LnkGen
when you open up wizard Cartman, you will be greeted by the best UI ever designed:
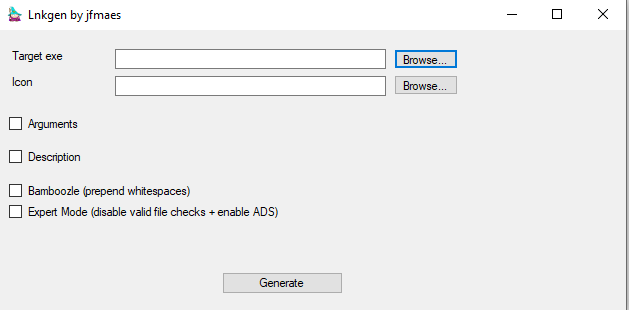
The UI has two modes, normal mode and expert mode. We will get to expert mode in a second, let’s first talk about usermode.
Usermode has two mandatory fields, a target exe and an icon. In usermode, file checks will be done (even if you type instead of using the file browser) to check if both files exist.
This means, in usermode you will only be able to create lnk files that target binaries you have installed on your system as well. this is an opsec consideration to avoid broken lnks (as you will be able to test run them on your own system).
Arguments and Description are optional, in case you want to leverage a LOLBIN and need command-line arguments, put them in the arguments field.
Description will provide mouseover text,should you hover over your lnk file.
Bamboozle will prepend whitespaces so the target exe is obfuscated as you cannot see it in the lnk properties anymore. keep in mind though that you will have MAX_PATH – 255 characters for your command line.
Let’s check it out in action shall we?
In this example, we will create a shortcut that mimics my favorite program of all times, MS Teams. In reality we will open cmd
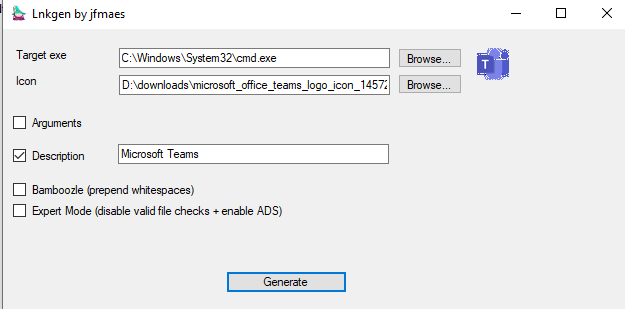
Generating the lnk results in the following:

Let’s inspect the properties:
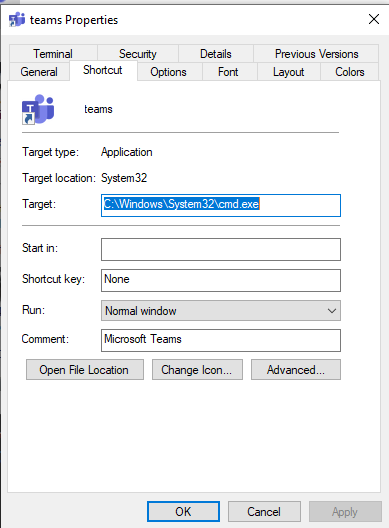
we can clearly see that this lnk will open a cmd and not Teams.
Let’s generate the same lnk again with the bamboozle option:
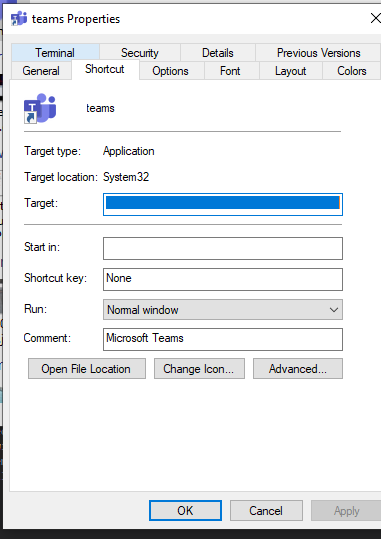
As you can see, the target here is blank 🙂 This is the Bamboozling.
Running the lnk will still pop cmd
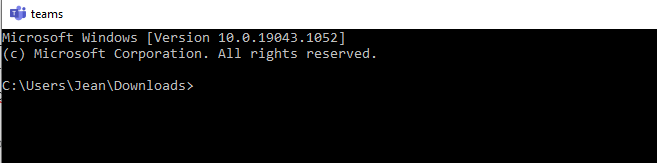
Expert mode
Expert mode will not enforce file checks on icon or target, which means you can craft lnk files that will only work on your target system (provided you know the absolute path of the target exe and icon). Additionally, expert mode gives you another interesting option, Alternate Data Streams
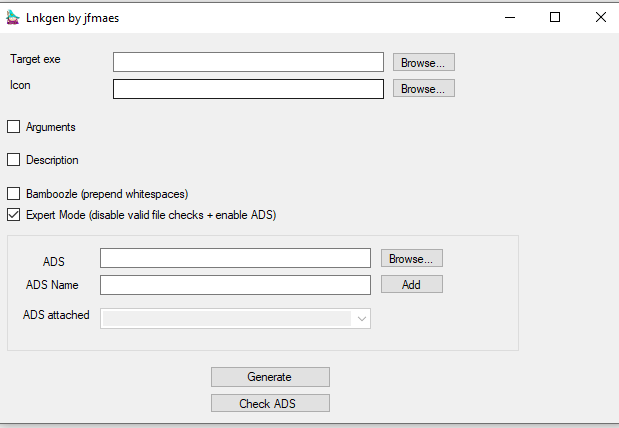
This gives you the possibility to add ADS to your lnk. Yes, ADS can be attached to anything, lnks are no exception. If you don’t know about ADS I suggest you don’t use this option.
ADS will also not ship with your lnk when your lnk bears the MOW (Mark of Web). So be mindful of that.
It also has a Check ADS button for sanity checks, Let’s create a lnk with an ADS and check if it is indeed attached to the lnk.
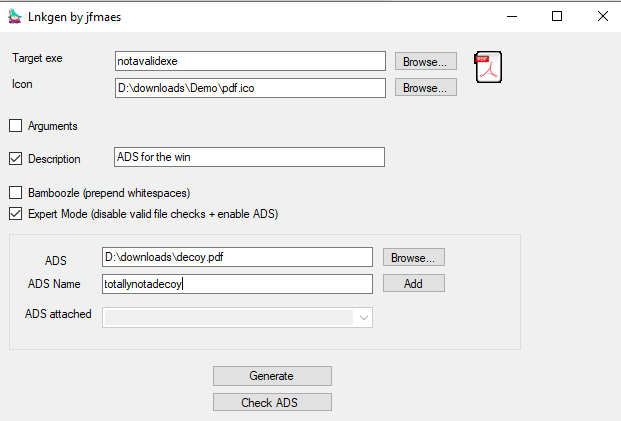
Pressing the Add button will clear the ADS and ADS Name fields and store your ADS in the ADS attached dropbox:
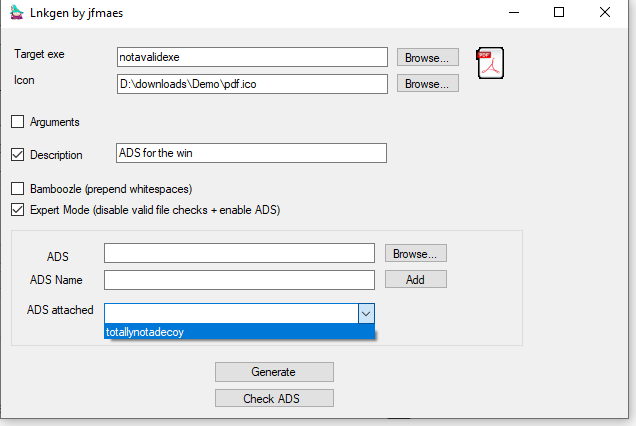
Generating the lnk will correctly generate the lnk (note the notavalidexe target)
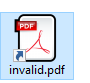
Clicking it will obviously not do anything other than say that my target is invalid:
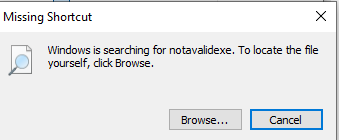
Let’s see if the decoy is indeed added using the Check ADS button:
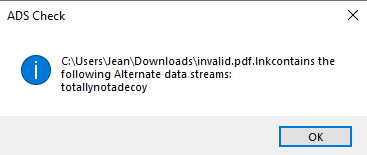
Multiple ADS’s can be added as well. Once again, shipping your lnk will strip the ADS unless you find a MOW bypass *cough* https://attack.mitre.org/techniques/T1553/005/ *cough*
Mitigations
Mail proxies should be able to be configured to disallow certain filetypes from external (and internal) sources. This is your first line of defence.
User awareness is your second line of defense, your users should be made aware time and time again to not just click random cr*p.
Of course, YARA master Florian Roth has a yara rule for lnk files found here: https://github.com/Neo23x0/signature-base/blob/master/yara/gen_susp_lnk_files.yar in case you want to hunt for this stuff.
Good application whitelisting can also help, as getting the lnk on a system is one thing, making it execute something malicious is another (very often relies on base64 decoding, or a LOLBIN)


[…] Click your shortcut and… you got pwnd: https://redteamer.tips/click-your-shortcut-and-you-got-pwned […]